The following is part of a series of thought pieces authored by members of the START Consortium. These editorial columns reflect the opinions of the author(s), and not necessarily the opinions of the START Consortium. This series is penned by scholars who have grappled with complicated and often politicized topics, and our hope is that they will foster thoughtful reflection and discussion by professionals and students alike.
We expect ISIL leadership to export behaviors, including targeting preferences, to its provinces outside of Iraq and Syria. This hypothesis, as self-evident as it may appear, is not necessarily specific enough to compel a decision-maker to allocate resources to minimize that risk. Where do I start, and how will I know if I am placing resources in the right place over time should I decide to act?
 Terrorism analysis has a long tradition focused on understanding the root cause of terrorism, terrorists’ motives, and in explaining terrorist behavior after the fact. Ultimately, the aim is to gain greater understanding of the adversary, allowing us to prevent terrorist events from occurring through a host of informed policies and operational programs. There is a large gap between analysis of motives and intentions, however, and predictive analysis.
Terrorism analysis has a long tradition focused on understanding the root cause of terrorism, terrorists’ motives, and in explaining terrorist behavior after the fact. Ultimately, the aim is to gain greater understanding of the adversary, allowing us to prevent terrorist events from occurring through a host of informed policies and operational programs. There is a large gap between analysis of motives and intentions, however, and predictive analysis.
Analysis of motives and intentions tend to be highly anecdotal, or highly subjective. The unintentional introduction of bias may skew conclusions and yield inaccurate assessments. Even in the best of cases, producing analysis using vetted and validated data without flaws is fraught, because “noise” in the data – such as inaccurate coding of attributes or locations -- can skew results. But often in the field of terrorism analysis, a politicized arena populated with clandestine actors, data are unstructured and of varying quality.
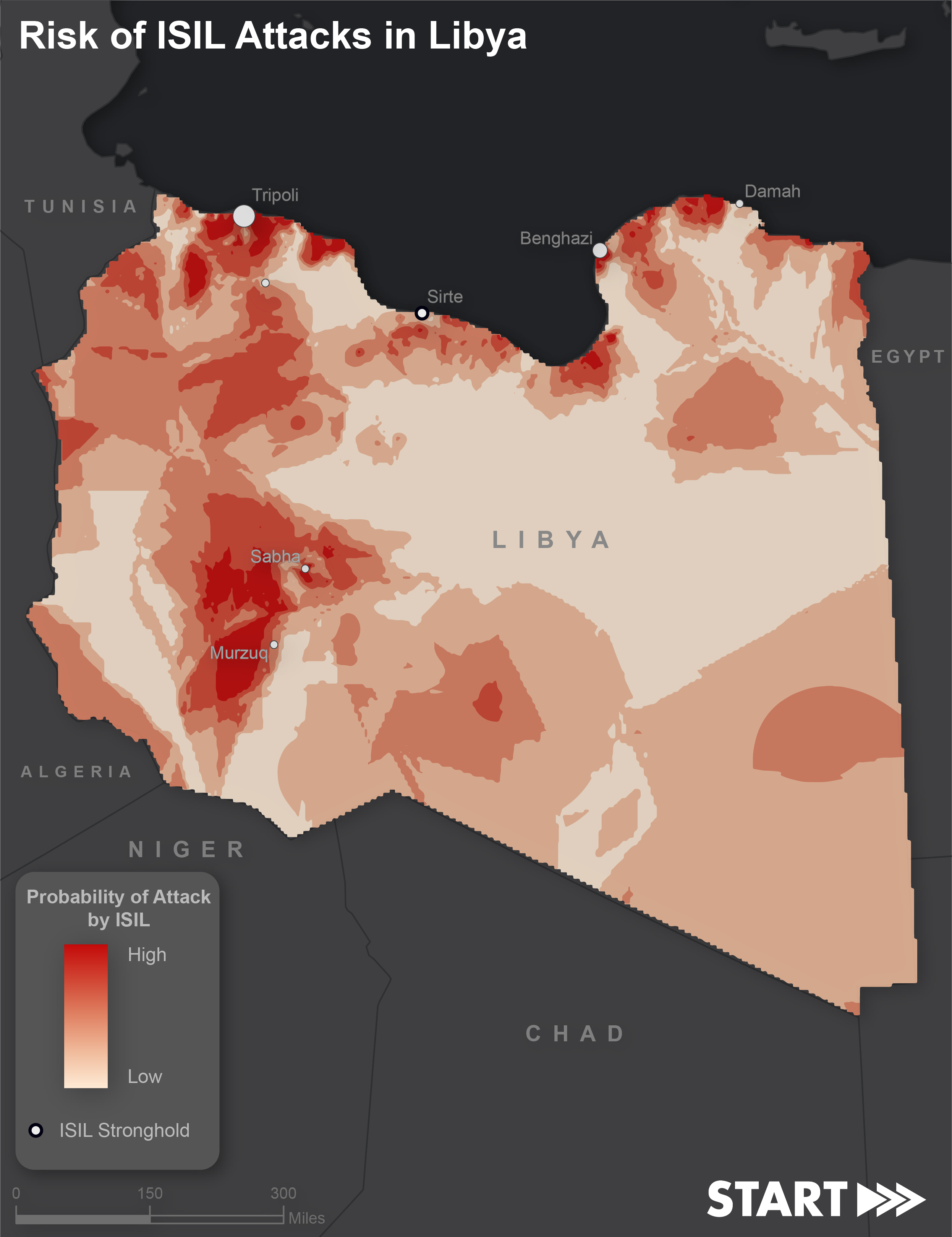
Given our hypothesis above, how can analytical tools be used to overcome these challenges and provide useful predictions of where ISIL may conduct attacks, and how can we test and refine this analysis over time? This preliminary study uses geostatistical analysis to identify the risk of Islamic State (ISIL) attacks in Libya based on previous attack patterns found in Syria and Iraq.
Applying What We Know to What We Want to Know
Bayesian statistical analysis, which favors updating and reassessing the probability of a new event occurring given a probability of historic event occurrences, offers a solution to some of our challenges. Using the Global Terrorism Database [1], which categorizes target type and group type, we can develop a probability of risk for places of interest (POI). If we look at ISIL attacks in Iraq and Syria from the first six months of 2015, we can calculate the probability of risk for specific target types based on the number of actual attacks when compared to the number of potential attack locations. That probability can then be applied to POI in Libya and spatially interpolated to show likelihood of attacks on Libyan infrastructure based on ISIL tactics in Syria and Iraq.
Attack data is first filtered to omit events that are not attributed to ISIL as well as events where kidnapping for ransom was observed as the primary motivation. In addition, any attack locations that could not be given a specific location -- such as an attack reported to have occurred “in a remote region” -- are omitted.
OpenStreetMap (OSM) [2] data is parsed to select POIs that could be incorporated into the target types established by the GTD methodology. Each targeted location is grouped within a specific target type (i.e. religious buildings, energy infrastructure, government buildings, etc.) because GTD target categories may not directly correlate with spatial data collected from OSM.
The Bayesian method is applied to the collected data from Iraq/Syria using Bayes’ Theorem applied to each sub category. The resulting risk probability is applied to OSM data points that correlate to locations in Libya based on the aforementioned ISIL attacks in Syria and Iraq.
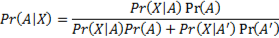
|
Pr(X|A) |
Chance of ISIL Attack given an Attack Occurs |
|
Pr(A) |
Chance of Attack at all (from total potential target population) |
|
Pr(A') |
Chance of No Attack at all (from total potential target population) |
|
Pr(X|A') |
Chance of ISIL Not Attacking given No Attack Occurs |
|
ISIL Attacks |
Potential Targets |
Pr(X|A) |
Pr(A) |
Pr(A') |
Pr(X|A') |
Pr(A|X) |
|
|
Religion |
25 |
2679 |
0.015547264 |
0.454222 |
0.545778 |
0.984453 |
1.30% |
|
Infrastructure |
14 |
1032 |
0.008706468 |
0.174975 |
0.825025 |
0.991294 |
0.19% |
|
Government |
161 |
696 |
0.100124378 |
0.118006 |
0.881994 |
0.899876 |
1.47% |
|
Natural Resources |
11 |
180 |
0.006840796 |
0.030519 |
0.969481 |
0.993159 |
0.02% |
|
Public Gathering Areas |
81 |
832 |
0.050373134 |
0.141065 |
0.858935 |
0.949627 |
0.86% |
|
Medical |
6 |
479 |
0.003731343 |
0.081214 |
0.918786 |
0.996269 |
0.03% |
|
Total |
298 |
5898 |
|||||
|
Total Attacks in Iraq/Syria |
1608 |
Assessment and Implications
An interpolation of the point data provides a spatial analysis of risk areas for Libya, absent of the use of any attack data in Libya. Without any input from ISIL attacks in Libya, we observe that areas around major cities have a higher likelihood of being attacked by ISIL much like we would expect. As attack data in Libya begins to aggregate, we can test our initial predictions, and incorporate these events into the analysis and recalculate to improve the risk profile for this specific study area.
Given that these results prove valid, it could be assumed that, with enough data points, a Bayesian model could be applied to other groups and locations. We can then apply a risk factor without having to first observe terrorist attacks in an emerging environment, and refine those risk factors as data becomes available, giving policymakers and counterterrorism professionals the confidence to initiate actions before civilian casualties begin to mount.
Citations
[1] National Consortium for the Study of Terrorism and Responses to Terrorism (START). (2013). Global Terrorism Database [Data file]. Retrieved from http://www.start.umd.edu/gtd on February 23, 2016. Note: Analysis is based on preliminary 2015 data not yet released for public use.
[2] OpenStreetMap. Contributor Geofabrik GmbH. Retrieved from http://www.geofabrik.de on November, 2015.
